APPLE QuickTime 7.6.7 Security Update for Windows
Apple has released a security update their Windows version of QuickTime 7.6.7 fixing one vulnerability. According to Apple this issue does not affect Mac OS X systems. APPLE iOS 4.0.2 Update for iPhone and iPod touch & 3.2.2 Update for iPad. Apple has released an update to fix comex’s recent .pdf exploit used by jailbreakme.com to jailbreak iDevices. You must use iTunes to update your device. This update is not available through Apple Software Update For more information on the security update Apple Security Updates web site: http://support.apple.com/kb/HT1222
APPLE-SA-2009-11-09-1 Security Update 2009-006 – Mac OS X v10.6.2 & 10.5.8
Along with this Snow Leopard update to 10.6.2, Apple also released a security update for OS X 10.5.8 client and server. The update includes numerous security updates and some feature enhancements, Apple also pulled support for Intel Atom processor which breaks Hackintosh Netbooks. The update is available via Software Update and Apple’s support downloads site.
iPhone SSH worms making the rounds
More variants of iPhone malware are showing up, some claiming to gather personal data from phones. Don’t be surprised with the source code for ikee circulating that more nefarious malware will be coming soon. JailBroken phone w/ alpine default pswd = pwned phone or a honeypot
In the past week or so at least four variants of simple worms that look for default ssh passwords on Jail Broken iPhones and replace the backgrounds screens have turned up. The one in the Netherlands is asking users to paypal 5 € to have it fixed. JD has an interview with the Australian writer ikee and two versions of the source code are available for research purposes. This variant scans a list of subnets for exploitable iPhones and pwns them replacing the background image with a custom one. Affected users are iPhone users that have JailBroken their phones and NOT changed their default ssh password of alpine. Take a look here at Saurik’s page with detailed instructions on changing your ssh password.
Apple Issues Java for Mac OS X 10.5 Update 5 – Patching several vulnerabilities
Apple issued a Java update Thursday patching several known vulnerabilities. The 161.35MB update is only applicable to Mac OS X Leopard version 10.5.8 or later (not Snow Leopard). Java SE 6 is updated to version 1.6.0_15, J2SE 5.0 is updated to version 1.5.0_20, and J2SE 1.4.2 is updated to version 1.4.2_22. While J2SE 5.0 and J2SE 1.4.2 support all Intel and PowerPC-based Macs, Java SE 6 requires a 64-bit Intel-based Mac.
Apple ships vulnerable Flash with Snow Leopard
 For those of you that have recently updated to OS X 10.6 Snow Leopard time to u[pgrade Flash Player. Apple downgraded your installation of Flash to an earlier version (version 10.0.23.1), which is known not to be secure and is not patched against various security vulnerabilities. The version you should be running is the latest version of Flash Player for Mac – 10.0.32.18
For those of you that have recently updated to OS X 10.6 Snow Leopard time to u[pgrade Flash Player. Apple downgraded your installation of Flash to an earlier version (version 10.0.23.1), which is known not to be secure and is not patched against various security vulnerabilities. The version you should be running is the latest version of Flash Player for Mac – 10.0.32.18
New Snow Leopard got Anti-Virus?
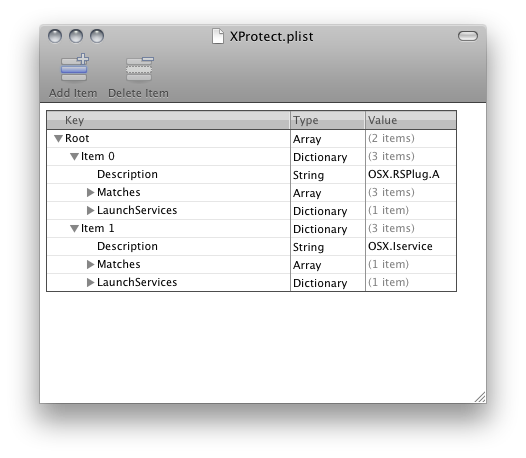
No not really, but it does check for a couple of the more common trojans. The last Developer seed of Snow Leopard Snow 10a421A and what we expect Apple to release on Friday contains a file XProtect.plist that checks for possible trojans. /System/Library/CoreServices/CoreTypes.bundle/Contents/Resources/XProtect.plist It contains five signatures for the two most active trojans, OSX.RSPlug that changes DNS settings and OSX.Iservice the one bundled with the pirated versions of iWork.
Security Update 2009-004 – Bind Vulnerability Fix
Apple issued a fix for the recent bind vulnerability. Good to see Apple releasing fixes fairly fast for known vulnerabilities. Available for: Mac OS X v10.4.11, Mac OS X Server v10.4.11, Mac OS X v10.5.8, Mac OS X Server v10.5.8 Impact: A remote attacker may be able to cause the DNS server to unexpectedly terminate Description: A logic issue in the handling of dynamic DNS update messages may cause an assertion to be triggered. By sending a maliciously crafted update message to the BIND DNS server, a remote attacker may be able to interrupt the BIND service. The issue affects servers which are masters for one or more zones, regardless of whether they accept updates. BIND is included with Mac OS X and Mac OS X Server but it is not enabled by default. This update addresses the issue by properly rejecting messages with a record of type ‘ANY’ where an assertion would previously have been raised. APPLE-SA-2009-08-11-1 Safari 4.0.3 Update
Hijacking Safari 4 Top Sites with Phish Bombs

It is possible for a malicious website to place arbitrary sites into your Top Sites view through automated actions. The attack technique makes use of javascript windows where in a small window is used to repeatedly browse to different sites that the attacker wants to add in your Top Sites list. This window is completely hidden using the window.blur function and user won’t know that is happening in the background. Please note that this attack is not possible using invisible iframes as Safari does not use iframe urls to decide Top Sites content.

